What is the best way to pass the CompTIA CySA+ CS0-001 exam? (First: Exam practice test, Second: leads4pass CompTIA expert.) You can get free CompTIA CS0-001 exam practice test questions here.
Or choose https://www.leads4pass.com/comptia-cysa-.html Study hard to pass the exam easily!
CompTIA CS0-001 Exam Video
Table of Contents:
- Latest CompTIA CySA+ CS0-001 google drive
- Effective CompTIA CySA+ CS0-001 exam practice questions
- Related CS0-001 Popular Exam resources
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest CompTIA CS0-001 google drive
[PDF] Free CompTIA CS0-001 pdf dumps download from Google Drive: https://drive.google.com/open?id=1SWIrLCSj4qgOfB86uKdQYM0Tdc3XrRlK
CySA+ (Plus) Cybersecurity Analyst Certification | CompTIA IT Certifications:https://www.comptia.org/certifications/cybersecurity-analyst
The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to configure and use threat detection tools, perform data analysis and interpret the results to identify vulnerabilities, threats, and risks to an organization, with the end goal of securing and protecting applications and systems within an organization.
CompTIA CySA+ is for IT professionals looking to gain the following security analyst skills:
- Perform data analysis and interpret the results to identify vulnerabilities, threats, and risks to an organization.
- Configure and use threat-detection tools.
- Secure and protect applications and systems within an organization.
Latest updates CompTIA CS0-001 exam practice questions
QUESTION 1
Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers
in the environment and needs to review all output files in order to determine which process running on one of the
servers
may be malware. Servers 1, 2 and 4 are clickable. Select the Server which hosts the malware, and select the process
which hosts this malware.
Instructions:
If any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have
completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the
Next button to continue.
Hot Area: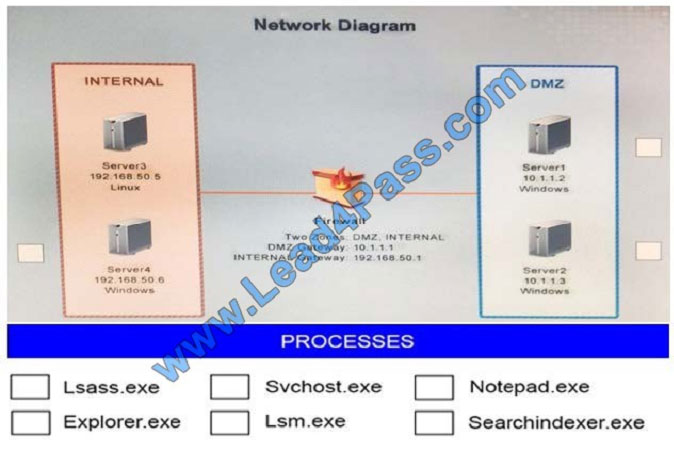
Correct Answer:
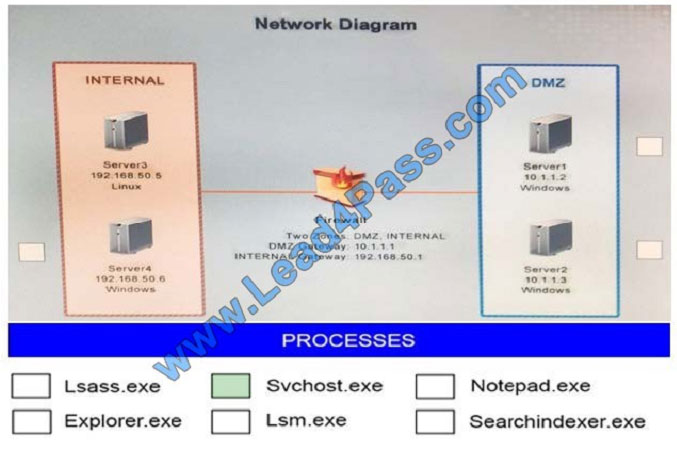
QUESTION 2
A security analyst is performing a review of Active Directory and discovers two new user accounts in the accounting
department. Neither of the users has elevated permissions, but accounts in the group are given access to the
company\\’s sensitive financial management application by default. Which of the following is the BEST course of
action?
A. Follow the incident response plan for the introduction of new accounts
B. Disable the user accounts
C. Remove the accounts\\’ access privileges to the sensitive application
D. Monitor the outbound traffic from the application for signs of data exfiltration
E. Confirm the accounts are valid and ensure role-based permissions are appropriate
Correct Answer: E
QUESTION 3
A cybersecurity analyst is currently investigating a server outage. The analyst has discovered the following value was
entered for the username: 0xbfff601a. Which of the following attacks may be occurring?
A. Buffer overflow attack
B. Man-in-the-middle attack
C. Smurf attack
D. Format string attack
E. Denial of service attack
Correct Answer: D
QUESTION 4
While preparing for a third-party audit, the vice president of risk management and the vice president of information
technology have stipulated that the vendor may not use offensive software during the audit. This is an example of:
A. organizational control.
B. service-level agreement.
C. rules of engagement.
D. risk appetite
Correct Answer: C
QUESTION 5
A cybersecurity analyst has received an alert that well-known “call home” messages are continuously observed by
network sensors at the network boundary. The proxy firewall successfully drops the messages. After determining the
alert was a true positive, which of the following represents the MOST likely cause?
A. Attackers are running reconnaissance on company resources.
B. An outside command and control system is attempting to reach an infected system.
C. An insider is trying to exfiltrate information to a remote network.
D. Malware is running on a company system.
Correct Answer: B
QUESTION 6
An organization uses Common Vulnerability Scoring System (CVSS) scores to prioritize remediation of vulnerabilities.
Management wants to modify the priorities based on a difficulty factor so that vulnerabilities with lower CVSS scores
may get a higher priority if they are easier to implement with less risk to system functionality. Management also wants to
quantify the priority.
Which of the following would achieve management\\’s objective?
A. (CVSS Score) * Difficulty = Priority Where Difficulty is a range from 0.1 to 1.0 with 1.0 being easiest and lowest risk to
implement
B. (CVSS Score) * Difficulty = Priority Where Difficulty is a range from 1 to 5 with 1 being easiest and lowest risk to
implement
C. (CVSS Score) / Difficulty = Priority Where Difficulty is a range from 1 to 10 with 10 being easiest and lowest risk to
implement
D. ((CVSS Score) * 2) / Difficulty = Priority Where CVSS Score is weighted and Difficulty is a range from 1 to 5 with 5
being easiest and lowest risk to implement
Correct Answer: A
QUESTION 7
A company has decided to process credit card transactions directly. Which of the following would meet the requirements
for scanning this type of data?
A. Quarterly
B. Yearly
C. Bi-annually
D. Monthly
Correct Answer: A
QUESTION 8
A security analyst suspects that a workstation may be beaconing to a command and control server. You must inspect
the logs from the company’s web proxy server and the firewall to determine the best course of action to take in order to
neutralize the threat with minimum impact to the organization.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you
have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select
the
Next button to continue.
Hot Area:
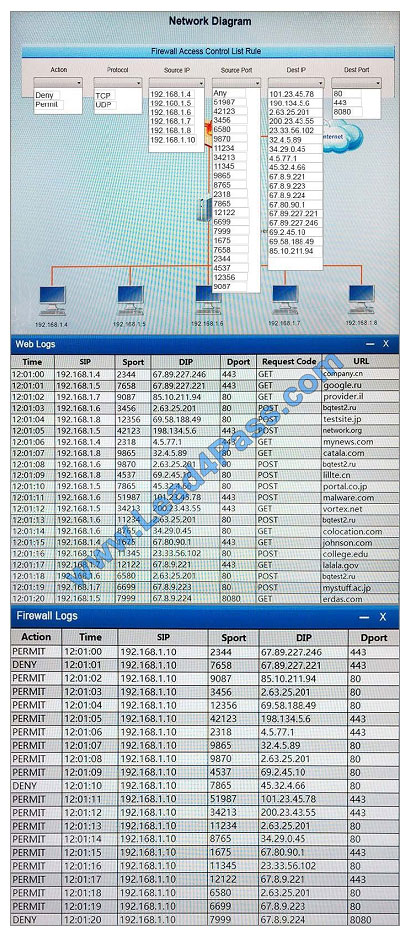
Correct Answer:
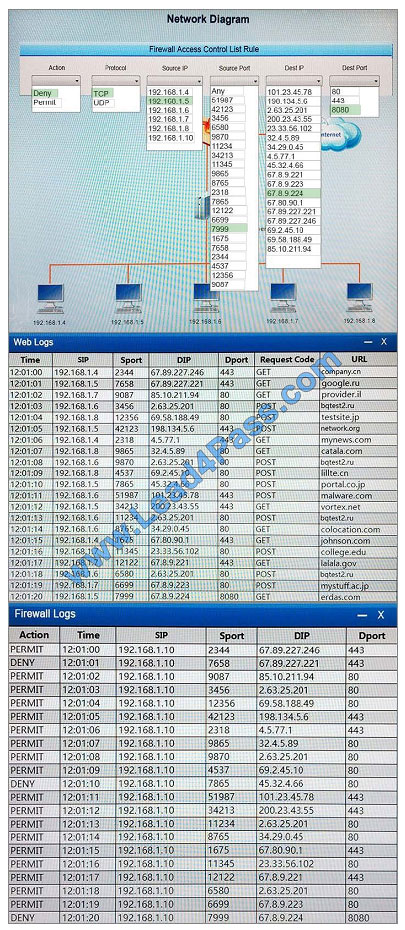
QUESTION 9
During a tabletop exercise, it is determined that a security analyst is required to ensure patching and scan reports are
available during an incident, as well as documentation of all critical systems. To which of the following stakeholders
should the analyst provide the reports?
A. Management
B. Affected vendors
C. Security operations
D. Legal
Correct Answer: A
QUESTION 10
An analyst reviews a recent report of vulnerabilities on a company\\’s financial application server. Which of the following
should the analyst rate as being of the HIGHEST importance to the company\\’s environment?
A. Banner grabbing
B. Remote code execution
C. SQL injection
D. Use of old encryption algorithms
E. Susceptibility to XSS
Correct Answer: B
QUESTION 11
Joe, an analyst, has received notice that a vendor who is coming in for a presentation will require access to a server
outside the network. Currently, users are only able to access remote sites through a VPN connection. Which of the
following should Joe use to BEST accommodate the vendor?
A. Allow incoming IPSec traffic into the vendor\\’s IP address.
B. Set up a VPN account for the vendor, allowing access to the remote site.
C. Turn off the firewall while the vendor is in the office, allowing access to the remote site.
D. Write a firewall rule to allow the vendor to have access to the remote site.
Correct Answer: B
QUESTION 12
A cybersecurity analyst is hired to review the security measures implemented within the domain controllers of a
company. Upon review, the cybersecurity analyst notices a brute force attack can be launched against domain
controllers that run on a Windows platform. The first remediation step implemented by the cybersecurity analyst is to
make the account passwords more complex. Which of the following is the NEXT remediation step the cybersecurity
analyst needs to implement?
A. Disable the ability to store a LAN manager hash.
B. Deploy a vulnerability scanner tool.
C. Install a different antivirus software.
D. Perform more frequent port scanning.
E. Move administrator accounts to a new security group.
Correct Answer: E
QUESTION 13
An analyst wants to use a command line tool to identify open ports and running services on a host along with the
application that is associated with those services and port. Which of the following should the analyst use?
A. Wireshark
B. Qualys
C. netstat
D. nmap
E. ping
Correct Answer: D
Related CS0-001 Popular Exam resources
| title | youtube | CompTIA | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| CompTIA CySA+ | leads4pass CS0-001 dumps pdf | leads4pass CS0-001 youtube | CySA+ (Plus) Cybersecurity Analyst Certification | https://www.leads4pass.com/cs0-001.html | 410 Q&A |
leads4pass Year-round Discount Code

What are the advantages of leads4pass?
leads4pass employs the most authoritative exam specialists from CompTIA, Cisco, Microsoft, IBM, EMC, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader!
Choose leads4pass to pass the exam with ease!

Summarize:
It’s not easy to pass the CompTIA CySA+ CS0-001 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. leads4pass.com provides you with the most relevant learning materials that you can use to help you prepare.